Executive Protection
Security Consulting
Private Investigation
Event
Security
Business Integrity
WELCOME TOPremier Risk Solutions
Premier Risk Solutions offers strategic insight into any threat facing an organization and provides world-class executive protection services. Through proper risk assessment, research and planning, a solid blueprint, and plan for comprehensive long-term risk mitigation and protective solutions can be formed. Our seasoned professional team, assembled from law enforcement/POST academy and/or military backgrounds, delivers a high degree of reliable, respectful, responsible, and professional service. We are here so you are safe, comfortable, and focused on the people or elements that are important to you.
PRIVATE SECURITY CONTRACTORProviding Services Tailored to Your Unique Needs
Trusted Clients
Countries Serviced
US Cities Serviced
Years of Experience

Your Private Security Partner
When you choose PRS as your private security contractor, you don’t get a typical bodyguard service. Our personal executive protection agents provide you a high degree of confidence that you’re protected from physical threats. And we know our clients also want a high degree of discretion regarding your reputation, which is why our agents are held to a strict code of ethics. Both professional and discreet, we ensure your reputation is protected and your private life remains private. Specializing in helping clients protect their families, physical property, reputation, and financial assets, we provide only the very best services to our clients.
PRIVATE SECURITY CONTRACTORProviding Services Tailored to Your Unique Needs
- Executive Protection
- Workplace Violence Prevention
- High-Risk Terminations
- Plant Closures
- Robbery Suppression
- VIP / Dignitary Security
- Asset Protection
- Travel Security
- Strike Force Security
- Special Event Security
- Security Guard Services
- Close Protection
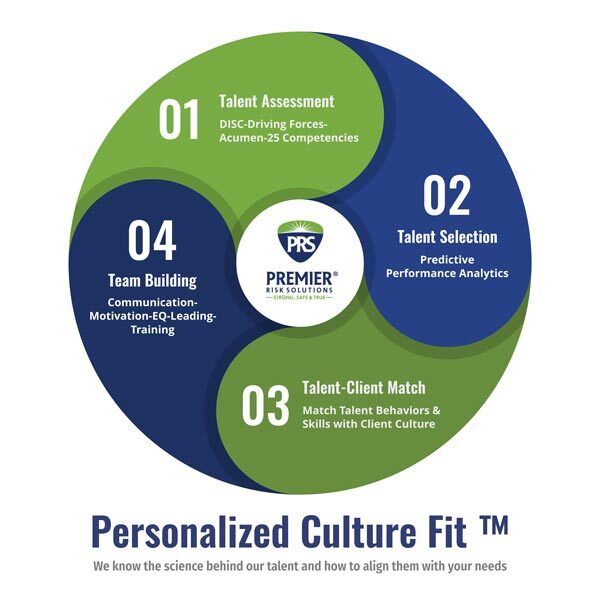
Personalized Culture Fit
PRS has developed its own Personalized Culture Fit™ program utilizing the science of self-methodologies to create custom job benchmarks to match our individual staff members to individual clients’ corporate culture and structure. Based on our experience working with Executive Protection providers, these are the top areas we deem most important for protection agents:
- Resiliency
- Time and Priority Management
- Personal Accountability
As a trusted private security contractor, each of our agents must provide a level of comfort and definitiveness to our clients. The longer-term implications of proper agent/client fit include reduced turnover, higher job satisfaction, more engaged employees and a more satisfied client. Relationships matter, and knowing our client’s unique needs is highly important when selecting an agent to deliver executive protective services.
Get to know the teamOur PRS Expert Team

Mike Delamere
President & Founder

Jeff Anspaugh
Chief of Staff

Thuy Loi
Vice President

Ira "Tre" Harge
EP Manager
GET YOUR TEAM WORKING RIGHTRequest a Call Back
Contact : To contact us, fill our short form or you can also send us an email and we’ll get in touch shortly, or Troll Free Number (206) 735-4956
Office Hours : 08:00am and 5:00pm Monday to Friday
Private Security Contractor
Delivering Exactly the Executive Protection Your Organization Needs & Wants
Serving the U.S. cities of Seattle, Bellevue, Albuquerque, Atlanta, Austin, Boston, Bozeman, Charleston, Charlotte, Chicago, Cleveland, Columbus, Cupertino, Dallas, Denver, Honolulu, Houston, Kansas City, Las Vegas, Los Angeles, Memphis, Miami, Minneapolis, Milpitas, Nashville, New York City, Oakland, Orange County, Orlando, Palo Alto, Phoenix, Portland, Reno, Sacramento, Salt Lake City, San Antonio, San Diego, San Francisco, San Jose, San Mateo, Sunnyvale, Tampa, Vancouver & Washington DC
Also serving select cities in Canada, Austria, Algeria, Argentina, Bangladesh, Brazil, Cambodia, Chile, China, Croatia, Czech Republic, Egypt, France, Germany, Greece, Guatemala, Hong Kong, Hungary, India, Indonesia, Ireland, Israel, Italy, Japan, Kenya, Latvia, Lithuania, Luxembourg, Malaysia, Malta, Mexico, Netherlands, Nigeria, Panama, Peru, Philippines, Poland, Portugal, Romania, Russia, Saudi Arabia, Slovenia, South Africa, South Korea, Spain, Singapore, Switzerland, Thailand, Tunisia, Turkey, Ukraine, United Arab Emirates, United Kingdom & Vietnam
Our BlogsLatest News
9 Special Event Security Best Practices: Ensuring a Safe and Memorable Experience
Hosting a special event, whether it’s a music festival, corporate conference, or sporting event, requires meticulous planning and execution. Ensuring the safety of attendees, staff, and performers is paramount. In this article, we’ll explore best practices for special event security to create a secure environment while maintaining a positive experience.
Preparing for California SB 553 Workplace Violence Prevention Implications in 2024
The enactment of CA SB 553, which takes effect July 1, 2024, creates the first general industry workplace violence prevention safety requirements in the United States. CA SB 553 requires California employers to develop their own workplace violence prevention plans as part of their Cal/OSHA Injury and Illness Prevention Plans or as a standalone Violence in the Workplace Prevention Program. Businesses must begin complying with the law on July 1, 2024.
Smart Digital Risk Detection in 2023 & Beyond
With increased cyberattacks to organizations of all sizes, digital risk detection is of paramount importance. What is digital risk detection? It’s the application of a tool or tools to access information on the social, surface, deep, and dark web. It’s seeking out exposures, data breach indicators, threats of violence, or otherwise reputationally damaging content to a brand or an individual’s (typically an executive’s) integrity.

